Jons
LinkedIn Leaks
500 Millions is the new unit when it comes to major companies data leaks.
#LinkedIn #leaks
https://www.courrierinternational.com/article/internet-les-donnees-de-500-millions-de-comptes-linkedin-en-vente-sur-un-forum

#StreetArt 2021



















binary comment 



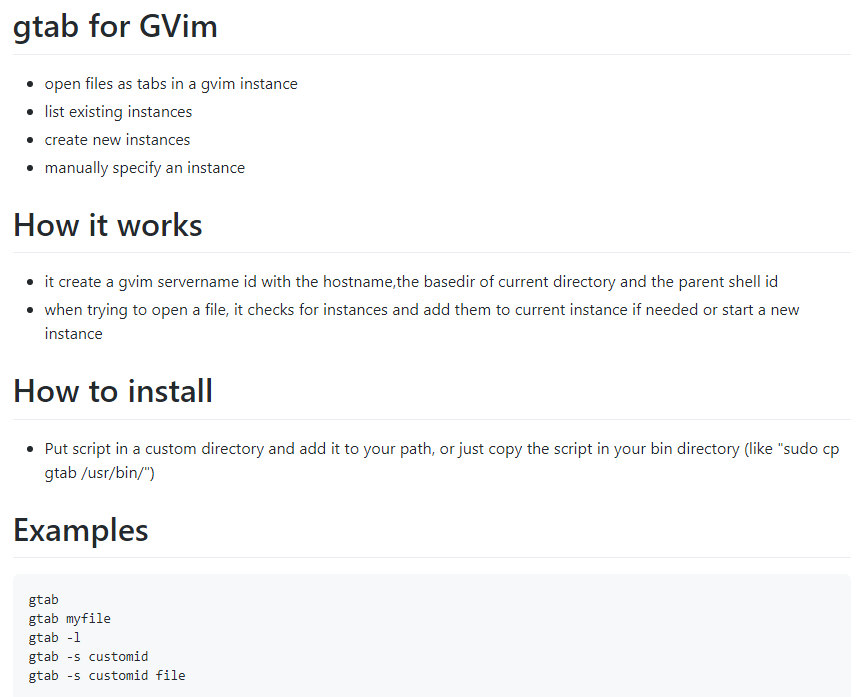
gtab for gvim
If you are using gvim a lot and love using tabs in it, then that little script is made for you !
You can get it at https://github.com/GullCode/gtabforgvim
Linux and Cygwin compatible
Animate your old photos with Deep Nostalgia
Deep Fake AI animate famous paintings / arts
Adding proxy to MSYS2
If you ever need to use a proxy when updating / installing packages in msys2 you’ll have to set the following environnement variables, and put them i.e in your .bash_profile :
# .bash_profile example
# Note: username and password have to be url encoded in case they contain special chars
export http_proxy=http://USERNAME:PASSWORD@proxy:port
# or like this if not user/password required
# export http_proxy=http://proxy:port
export https_proxy=$http_proxy
export ftp_proxy=$http_proxy
export rsync_proxy=$http_proxy
# if you need a proxy ignore list
export no_proxy="localhost,127.0.0.1,localaddr,.yourlocaldomain.ext,.local"MSYS2 ALLEGRO5 Setup
I’ve set up my last allegro 5 install + compilers in less than 15 minutes.
1) download and install msys2 ( https://www.msys2.org/ )
Now launch the msys2 terminal and copy pasta the followings:
#UPDATE MSYS2
pacman -Syu
#INSTALL GCC 32 & 64BITS
pacman -S --needed base-devel mingw-w64-i686-toolchain mingw-w64-x86_64-toolchain git subversion mercurial mingw-w64-i686-cmake mingw-w64-x86_64-cmake
#INSTALL ALLEGRO5 32 & 64BITS
pacman -Sy mingw32/mingw-w64-i686-allegro mingw64/mingw-w64-x86_64-allegro
#INSTALL ALLEGRO5 64BITS DEPENDENCIES
pacman -Sy mingw-w64-i686-dumb mingw-w64-i686-flac mingw-w64-i686-opusfile mingw-w64-i686-freetype mingw-w64-i686-libjpeg-turbo mingw-w64-i686-libpng mingw-w64-i686-libvorbis mingw-w64-i686-libwebp mingw-w64-i686-openal mingw-w64-i686-physfs
#INSTALL ALLEGRO5 32BITS DEPENDENCIES
pacman -Sy mingw-w64-x86_64-dumb mingw-w64-x86_64-flac mingw-w64-x86_64-opusfile mingw-w64-x86_64-freetype mingw-w64-x86_64-libjpeg-turbo mingw-w64-x86_64-libpng mingw-w64-x86_64-libvorbis mingw-w64-x86_64-libwebp mingw-w64-x86_64-openal mingw-w64-x86_64-physfs533 million Facebook users’ phone numbers and personal data have been leaked online
That’s quite a leak if you’re asking me.
https://www.businessinsider.fr/us/stolen-data-of-533-million-facebook-users-leaked-online-2021-4
CYGWIN: list all process arguments
A few days ago I had to list the arguments for specific process.
While finding it using “ps -aef | grep ‘processname'” and getting the information is trivial under linux, it is not the case using cygwin, which is only reporting process name and pid when calling “ps”.
A lot of solutions involve installing cygwin packet, like pstree.
Another solution is to search the /proc/pid/cmdline files, like here:
grep -a /proc/*/cmdline | xargs -0
/proc/1990/cmdline:/bin/sh /usr/bin/startxwin
/proc/2016/cmdline:xinit /etc/X11/xinit/startxwinrc — /usr/bin/XWin :0 -multiwindow -auth /home/user/.serverauth.1990
/proc/2017/cmdline:/usr/bin/XWin :0 -multiwindow -auth /home/user/.serverauth.1990
/proc/2023/cmdline:/usr/bin/xwin-xdg-menu
/proc/2035/cmdline:dbus-launch –sh-syntax –exit-with-session
/proc/2036/cmdline:/usr/bin/dbus-daemon –fork –print-pid 5 –print-address 7 –session
/proc/2046/cmdline:/usr/libexec/gam_server
/proc/2512/cmdline:mintty
/proc/2513/cmdline:bash
/proc/3441/cmdline:grep –color -a /proc/1990/cmdline /proc/2016/cmdline /proc/2017/cmdline /proc/2023/cmdline /proc/2035/cmdline /proc/2036/cmdline /proc/2046/cmdline /proc/2512/cmdline /proc/2513/cmdline /proc/3441/cmdline /proc/self/cmdline
/proc/self/cmdline:grep –color -a /proc/1990/cmdline /proc/2016/cmdline /proc/2017/cmdline /proc/2023/cmdline /proc/2035/cmdline /proc/2036/cmdline /proc/2046/cmdline /proc/2512/cmdline /proc/2513/cmdline /proc/3441/cmdline /proc/self/cmdline
To restrain it to a particular process i.e XWin, excluding grep command:
grep -a “XWin” /proc/*/cmdline |xargs -0 |grep -v grep
/proc/2016/cmdline:xinit /etc/X11/xinit/startxwinrc — /usr/bin/XWin :0 -multiwindow -auth /home/user/.serverauth.1990
/proc/2017/cmdline:/usr/bin/XWin :0 -multiwindow -auth /home/user/.serverauth.1990
Nilorea Library is part of GitHub Arctic Code Vault
Just wanted to say that my own public repo for NiloreaLibrary is part of the vault, and a copy of it is in the archive located in a decommissioned coal mine in the Svalbard archipelago, closer to the North Pole than the Arctic Circle. GitHub captured a snapshot of every active public repository on 02/02/2020 and preserved that data in the Arctic Code Vault.
More infos:
Stack walking, assembly analysis and dll injection to speed up a game loading time
Follow the link to read how the guy did it, step by step and with the tools he used. It’s an impressive work on top of it being nicely documented.
“How I cut GTA Online loading times by 70%”
T0ST 2021-02-28 => https://nee.lv/2021/02/28/How-I-cut-GTA-Online-loading-times-by-70/
Did Shnorr broke RSA ?
A recently published paper by a reputable German mathematician and cryptographer has garnered widespread attention for its claim to have destroyed the RSA algorithm. However, many people are skeptical. Join us as we discuss the paper’s content, the proposed methodology, and the public discussion it has generated.
https://sectigo.com/resource-library/root-causes-154-did-claus-peter-schnorr-just-break-rsa
#RSA #TLS #SSL #SHNORR
Sunset
Today was such a nice day, even the sun took it’s time to go down !







